In the previous series, we focused on setting up Duo SSO. This time, we’re diving into Palo Alto Networks’ Admin UI configuration with Duo SSO. This guide will help PAN-OS administrators implement secure access controls using Duo’s robust authentication features.
Configuring Palo Alto Networks – Admin UI with Duo SSO
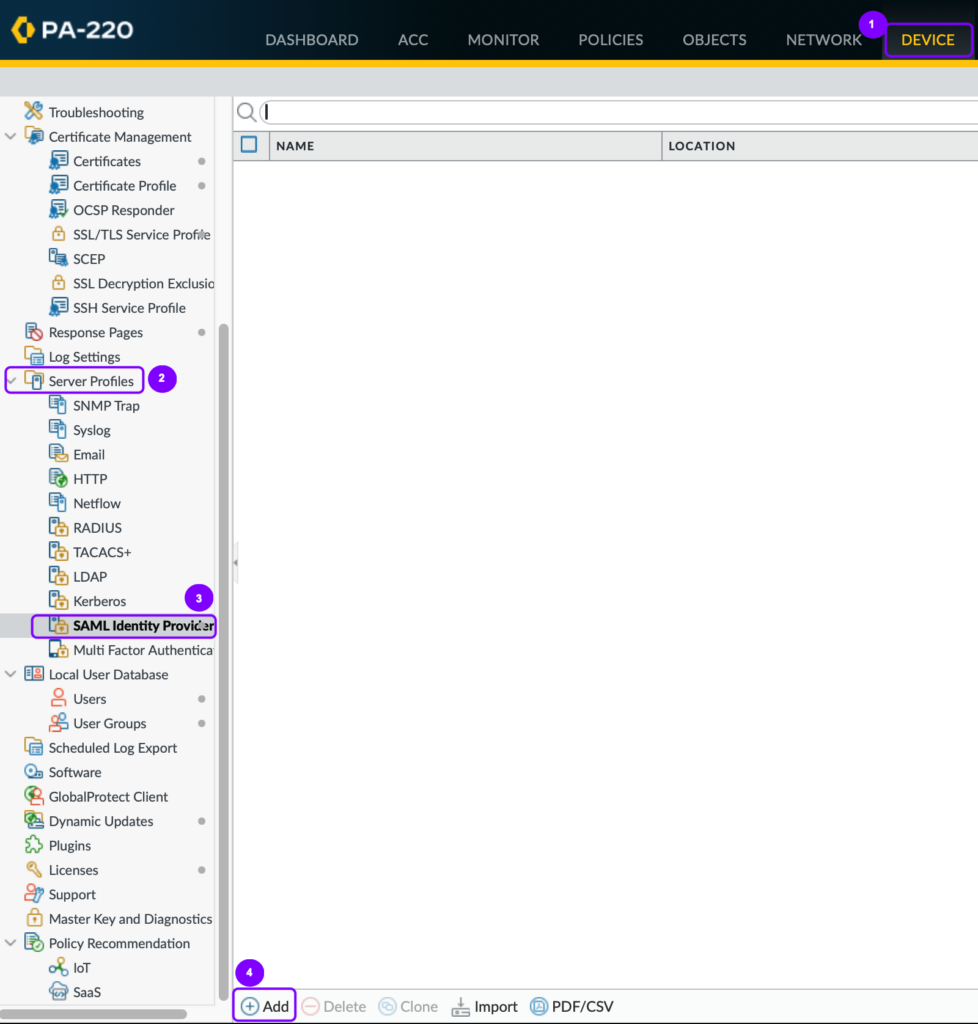
- Log on to the Palo Alto Admin Panel:
- As an Administrator, click the Device tab.
- Select Server Profiles > SAML Identity Provider.
- Click Add.
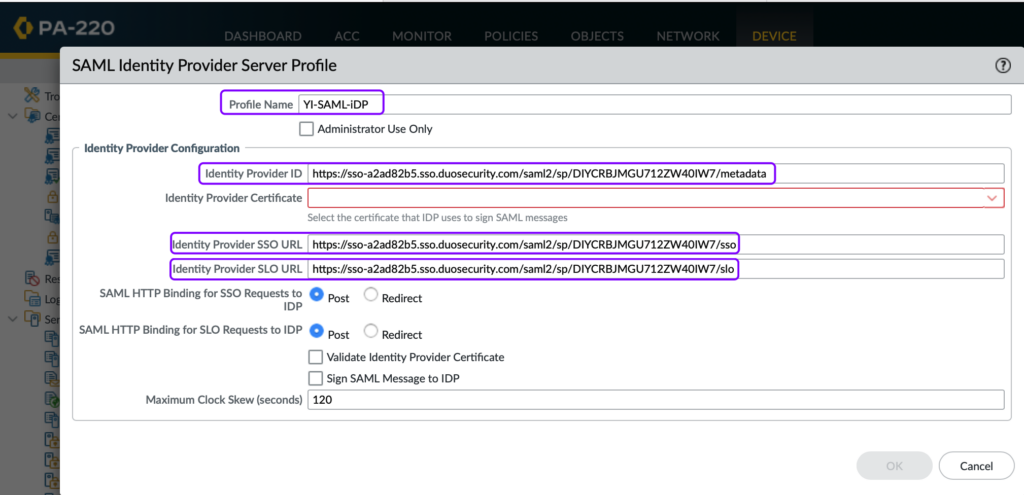
- Enter Profile Details:
- Enter a Profile Name of your choice.
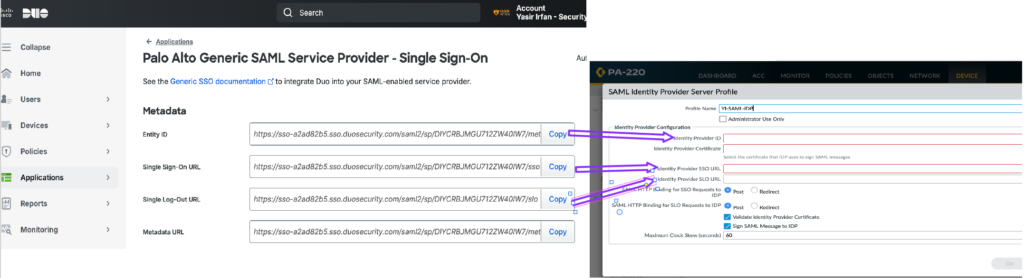
- Copy the details from the Palo Alto Generic SAML Service Provider – Single Sign-On created in the Duo Admin Panel to the Server Profile.
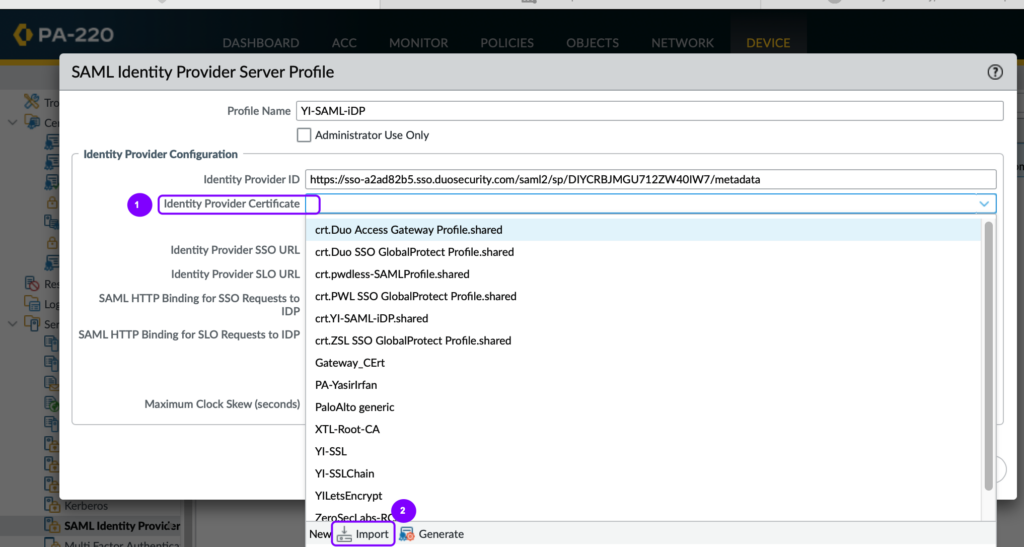
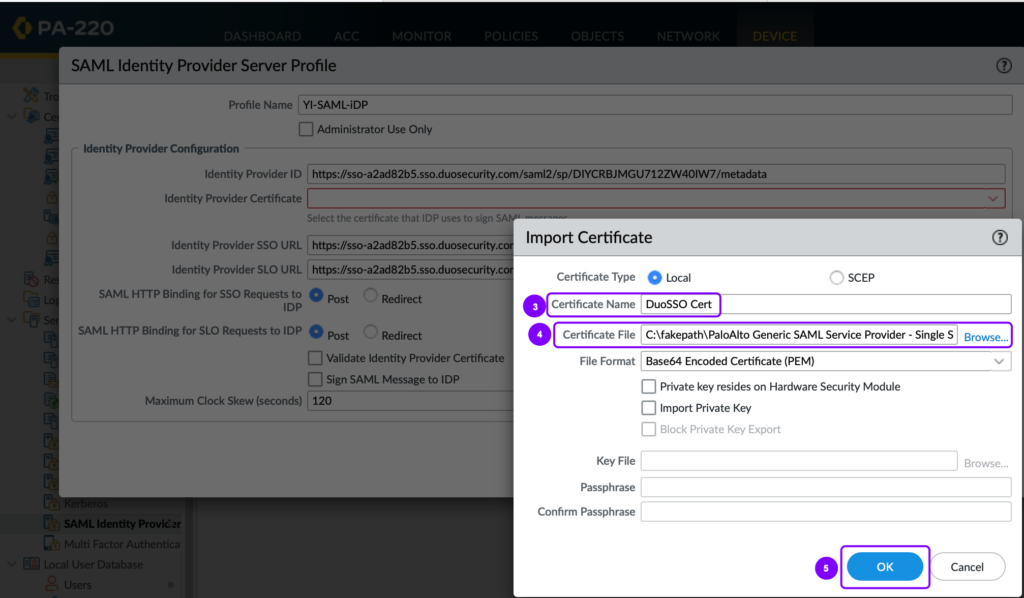
- Import the Identity Provider Certificate downloaded from the Duo Admin Panel (downloaded in step 7 of the previous article)
Table 4 : SAML Identity Provider Server Profile
| Entity ID | Identity Provider ID |
| Single Sign-on URL | Identity Provider SSO URL |
| Single Sign-Out URL | Identity Provider SLO URL |
- Add an Authentication Profile:
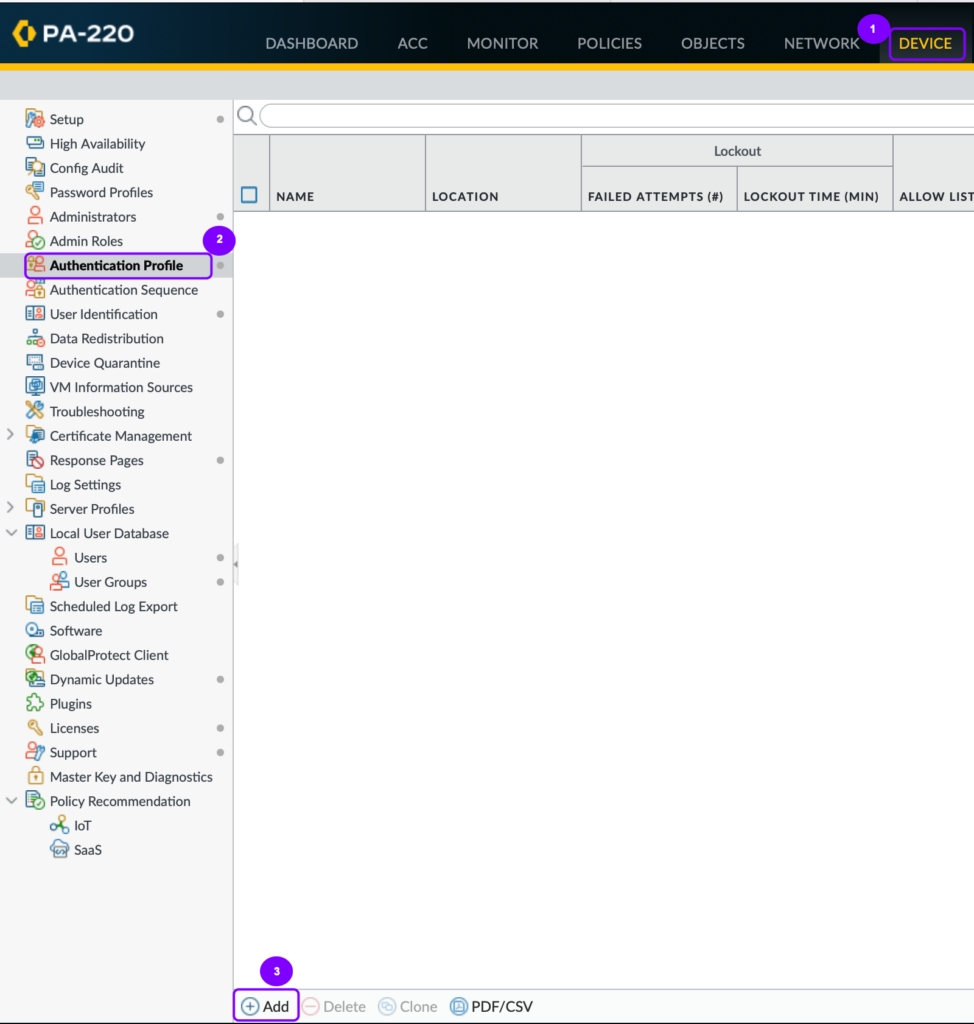
- Navigate to Device > Authentication Profile.
- Click Add.
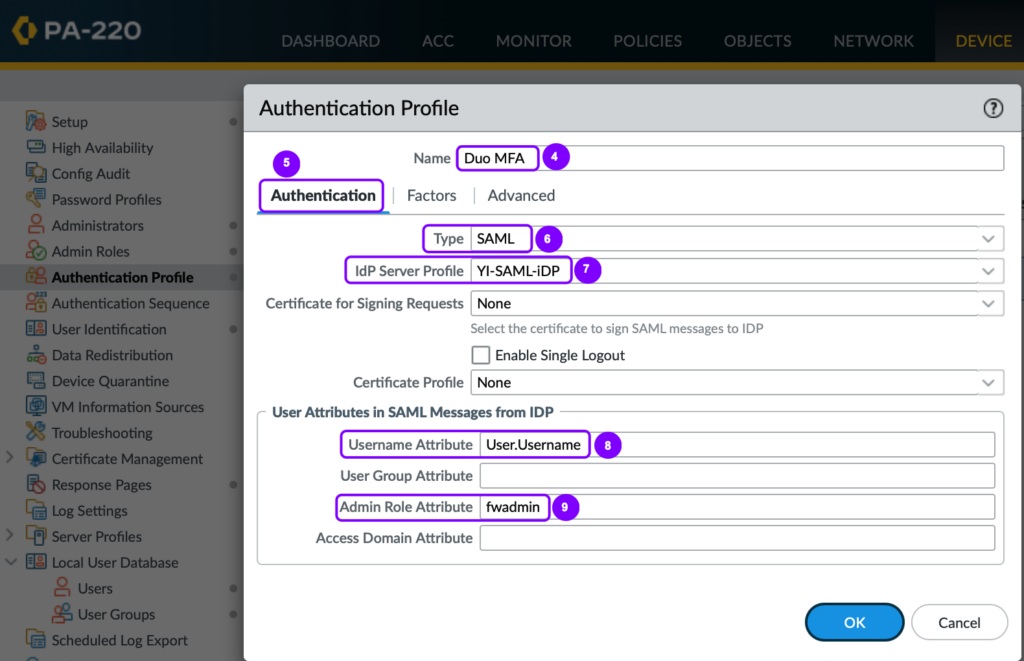
- Enter the following information in the Authentication tab and click OK:
Table 5 : Authentication Profile – Authentication tab
| Name | Duo MFA |
| Type | SAML |
| IdP Server Profile | YI-SAML-iDP |
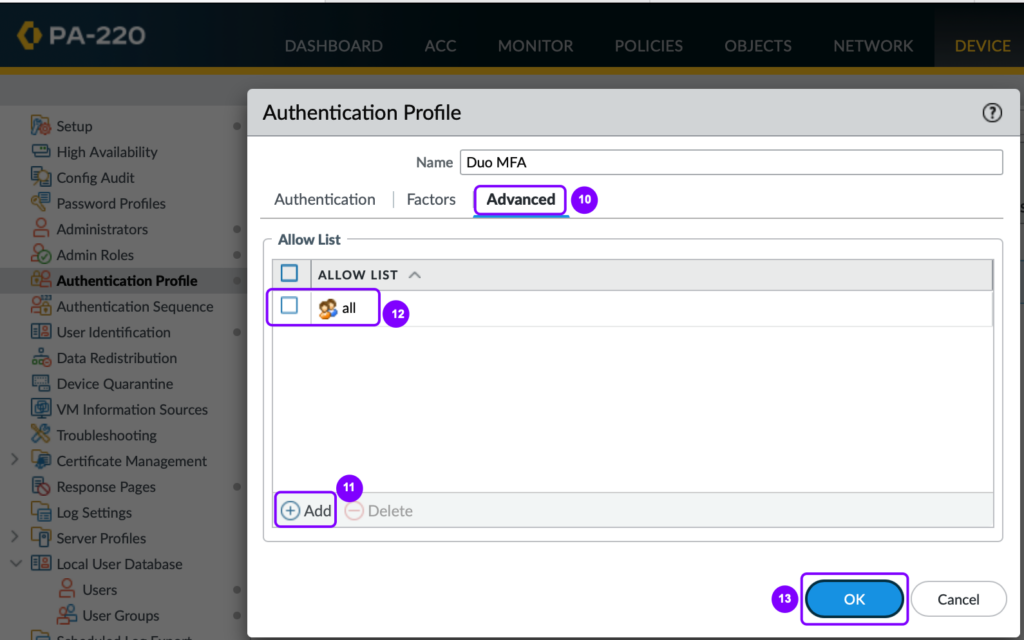
Table 6 : Authentication Profile – Advanced tab
| ALLOW LIST | all |
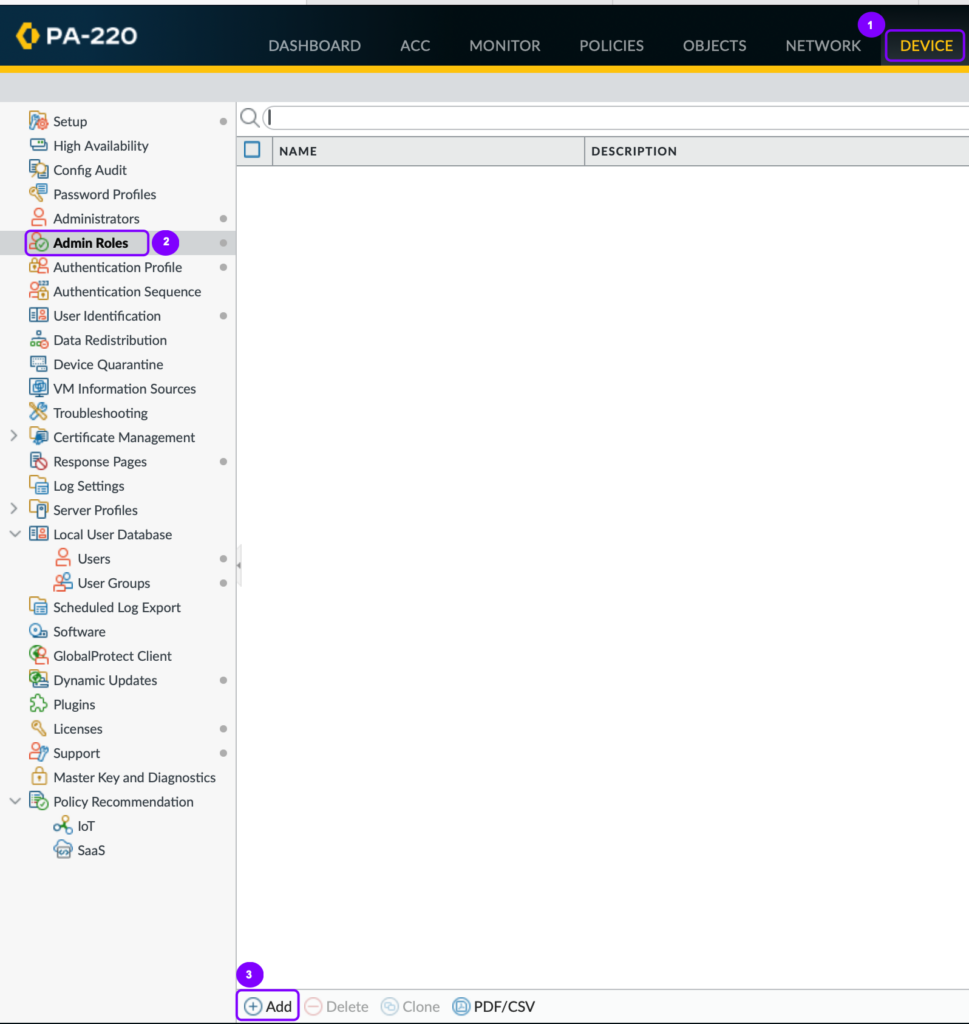
- Add an Admin Role:
- Navigate to Device > Admin Role.
- Click Add.
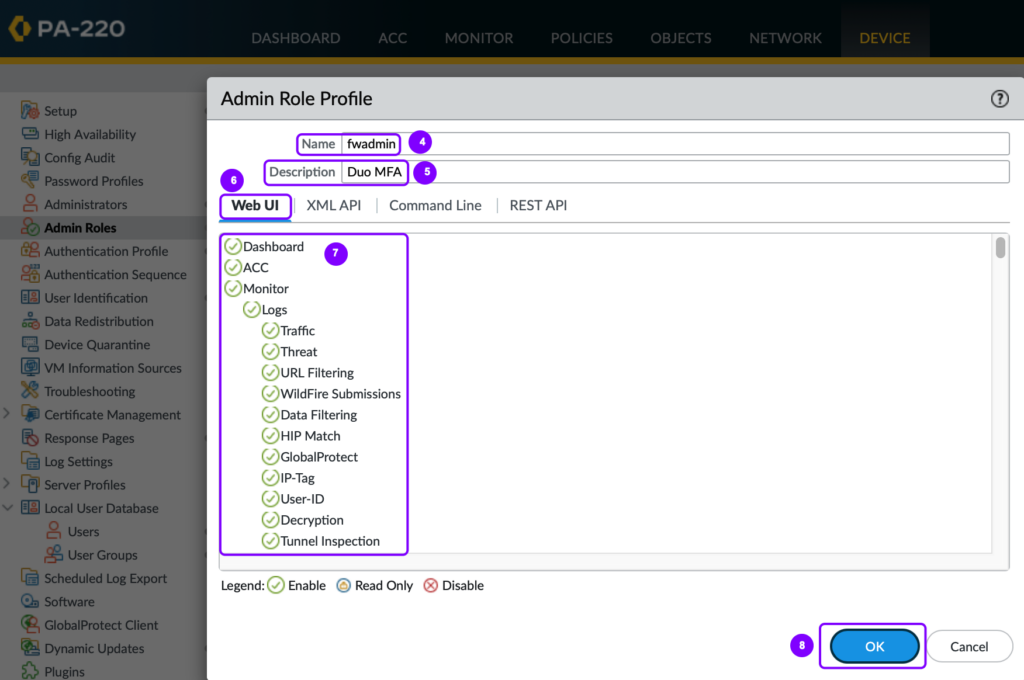
- Provide the Admin Role name and click OK.
- Enable Administrators to Use SAML SSO:
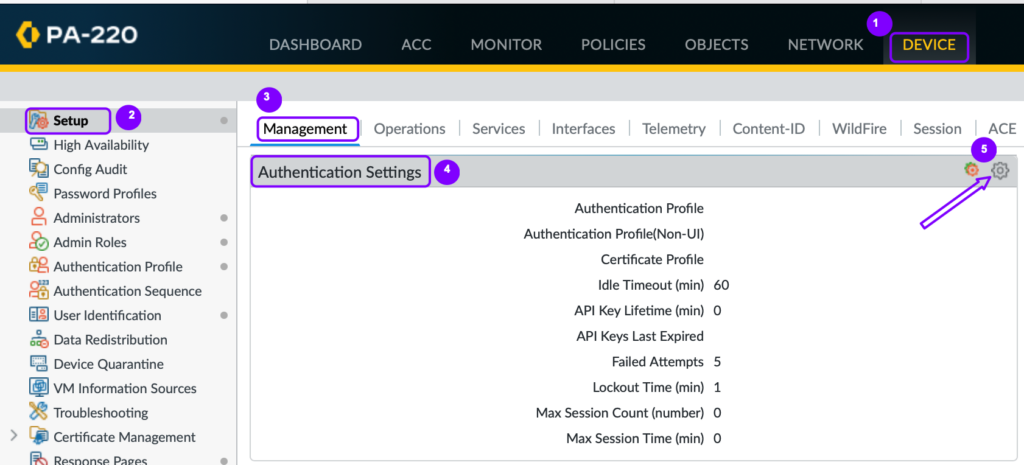
- Navigate to Device > Setup.
- In the Setup pane, select the Management tab.
- Under Authentication Settings, click the gear icon.
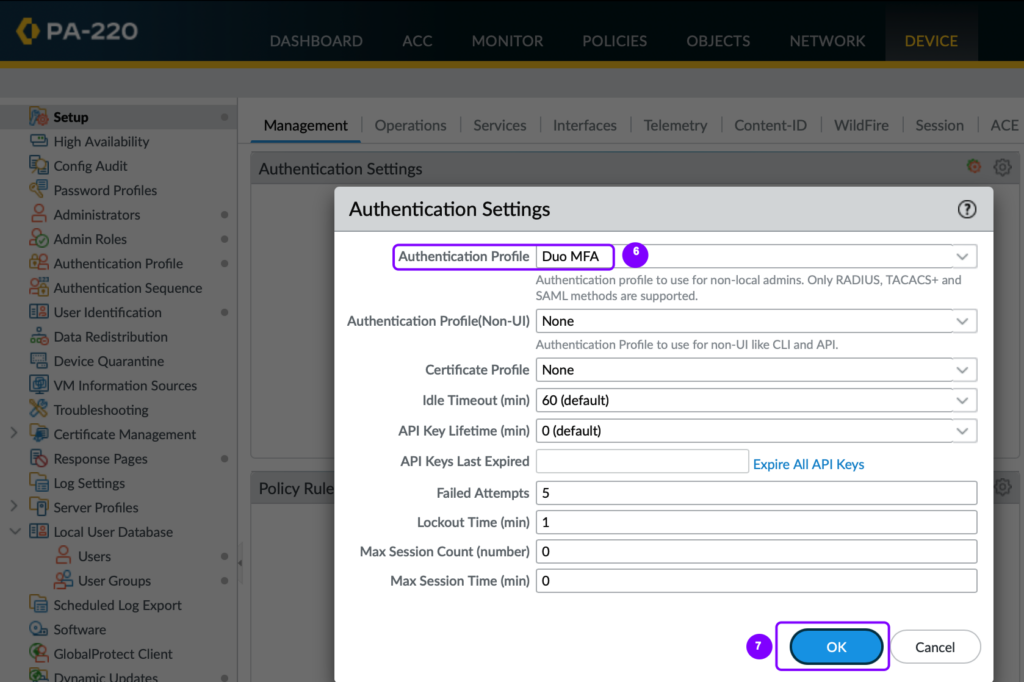
Please ensure to click commit after every step to save the configuration changes.

Following the outlined steps, we successfully integrated Palo Alto Network security appliances, including Firewalls and Panorama, with Duo MFA via Duo SSO. We’ve also enabled advanced Duo security features such as risk-based authentication, trusted endpoints, and passwordless authentication. Now, let’s validate the configuration by logging into the Palo Alto Admin UI.
- Log in to Palo Alto Network Firewall Admin Panel:
- Click Use Single Sign-On.
- Enter your login credentials.
- Click Continue to complete the Duo SSO login process.
- A Touch ID prompt will appear as the passwordless feature is enabled in the Application Policy within the Duo Admin Panel


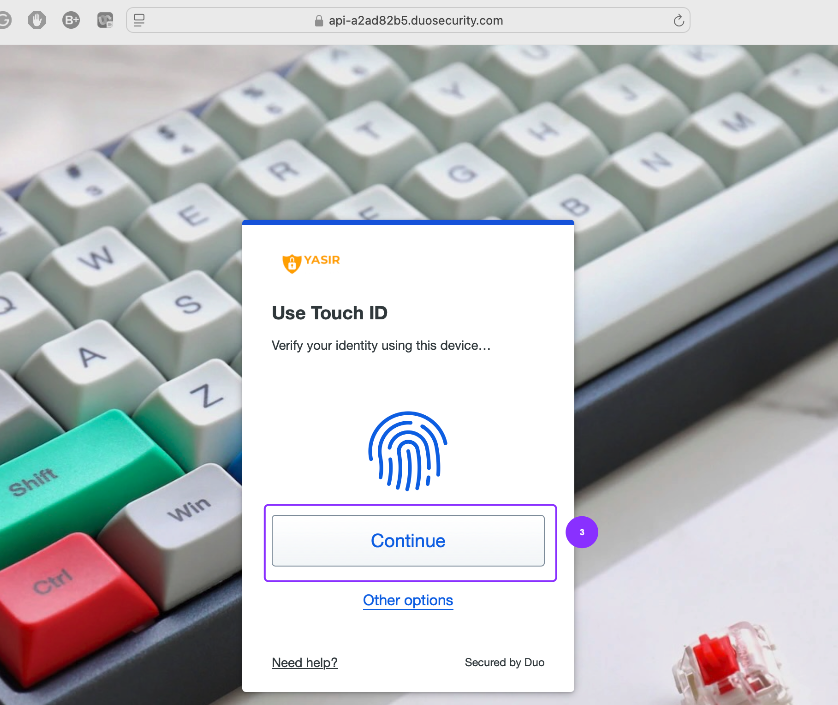
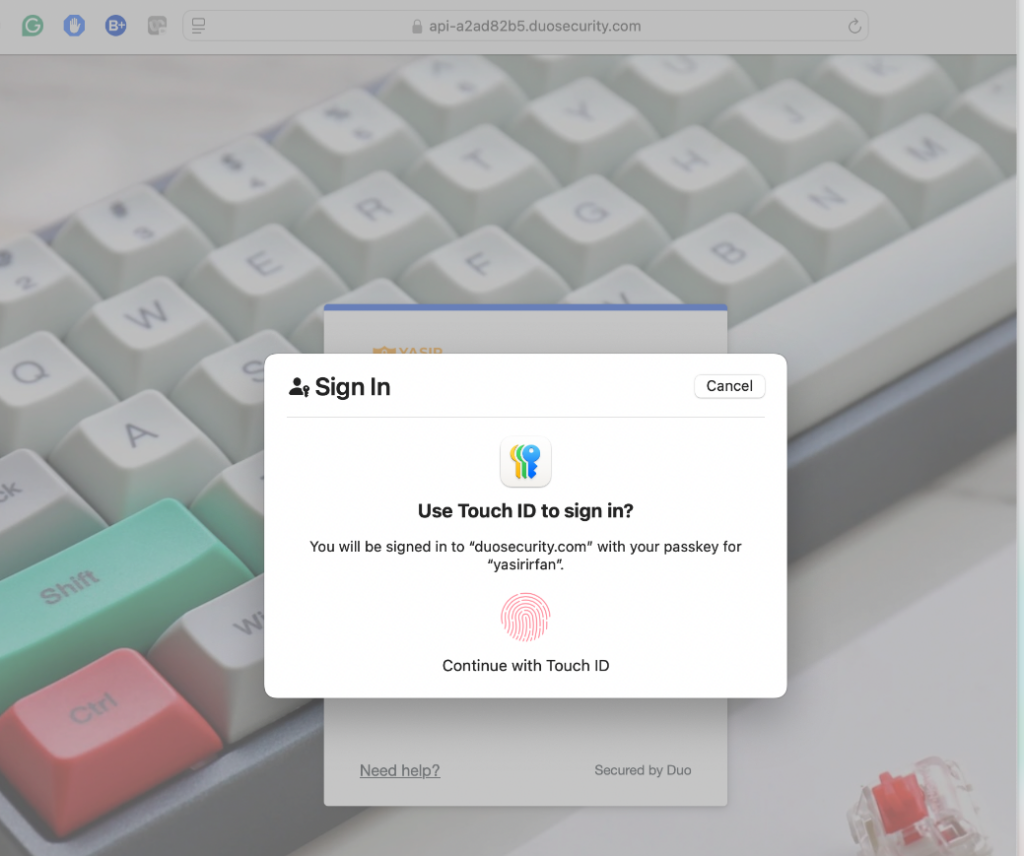
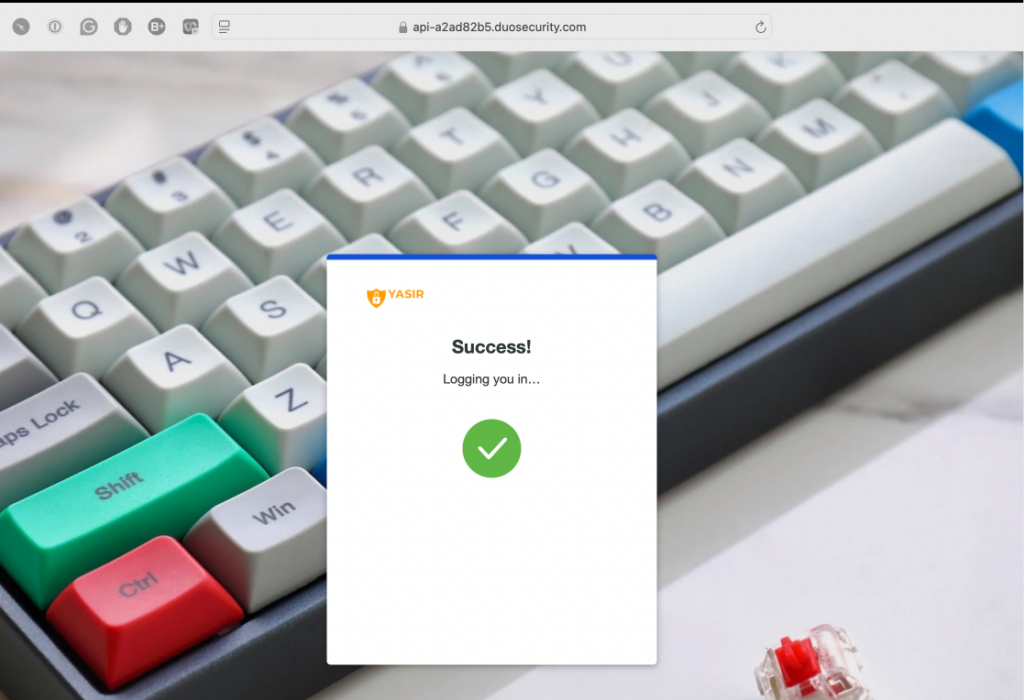
Upon successful passwordless login, the user will be directed to the Palo Alto Admin UI for Firewall or Panorama administration. Let’s validate the login activity logs in both the Duo Admin Panel and the Palo Alto Admin UI.
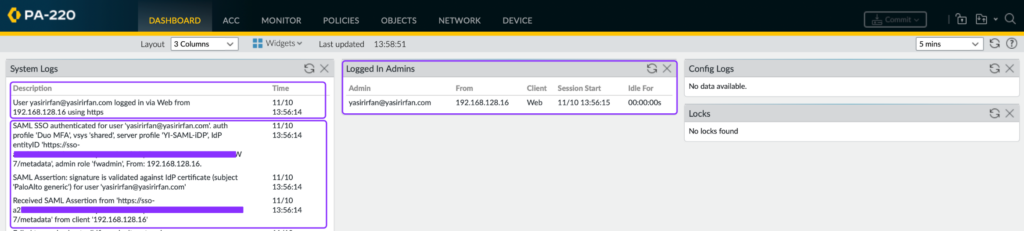
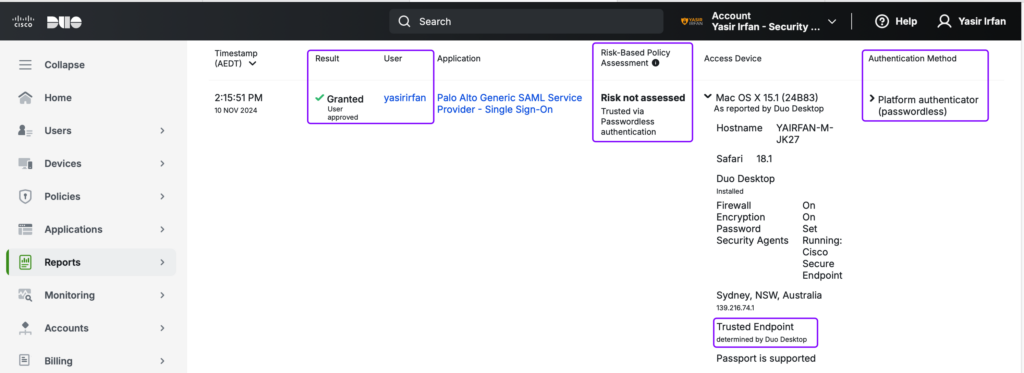
After analyzing the logs, we confirmed that access to the Palo Alto Admin UI was successfully granted using passwordless authentication. The Duo policy further enhances security by enforcing access from a Trusted Endpoint.
The Duo Passwordless feature supports the following authentication methods:
• Windows Hello on compatible Windows devices
• Touch ID on compatible macOS devices
• Face ID or Touch ID on compatible iOS and iPadOS devices
• Android Biometrics, including Pixel fingerprint or facial recognition, and Samsung fingerprint or facial recognition
• WebAuthn FIDO2 security keys with biometric or PIN verification, such as those from Yubico or Feitian
• Duo Push authentication requests sent to Duo Mobile on Android or iOS devices secured with biometric, PIN, or passcode unlocking